| NBM Filter Management for BorderManager 3.8 SP3 
Posted: 2 Jun 2005
This Tip discusses the implementation scenarios and different usage
perspectives of a new feature provided with the latest support pack (SP3) of
BorderManager 3.8 - the Filter Management Wizard, also referred to as the
Firewall Wizard. This feature helps you configure filters and exceptions for
services easily. The Tip details the configuration of filters using the
wizard, by using several deployment scenarios, a number of screen shots, and
some simple troubleshooting information.
Introduction
BorderManager includes packet-filtering capability, which secures all the
traffic through the BorderManager server. This feature helps system
administrators to allow only desired traffic to and from the firewall by
configuring service exceptions and at the same time restrict undesired traffic
by configuring appropriate filters.
In the previous versions of BorderManager (NBM 3.7 and prior), packet
filtering was configured on the server using filtcfg. Remote management and
configuration of filters and exceptions through iManager was introduced with NBM
3.7. Known as NBM Access Management, it allowed users to add packet filters and
exceptions through iManager. However, this utility remained similar to filter
configuration using filtcfg; the main difference being that filter management
was GUI-driven. A user using the NBM Access Management utility still needs to go
through the entire list of services available on the server while selecting the
appropriate exception. That user is also expected to have a thorough knowledge
of how each service type works.
With the release of NBM 3.8 SP3, users now have the Firewall Wizard, which
solves this shortcoming and adds many more features. The Firewall Wizard is an
iManager-based wizard that enables users to implement packet filtering on a
BorderManager server in a more comprehensive and organized manner.
The default filters block all the traffic from the Internet or any interface
of the BorderManager server to the public interface of the BorderManager server,
and vice versa. Service exceptions can then be created to allow specific
services through the BorderManager server. The Firewall Wizard provides the
facility to create exceptions in one shot to allow access to the required
services.
Note: Filters are still stored only in the Directory Services.
New Features of the Firewall Wizard
Figure 1 and Figure 2 demonstrate the differences in NBM Access Management
between the versions available prior to NBM 3.8SP3 and the new Firewall
Wizard.

Figure 1 - NBM Access Management available with versions prior to NBM
3.8SP3
Figure 2 - Firewall Wizard or NBM Filter Management
The major difference between the Firewall Wizard and NBM Access Management
and filtcfg, for the end user, is how the filters have been grouped. In the
Firewall Wizard, the logical separation of services and exceptions enables you
to set up packet filtering according to the requirements of the network. This
makes it easier to configure filters depending on the service exceptions
required to pass through the network and block others.
The Easy Filter Configuration option in the Firewall Wizard adds exceptions
for the required services through the firewall in a few clicks. Under this task,
services are logically grouped together under three tabs: NBM service
exceptions, On-Server service exceptions, and Off-Server service exceptions.
The Filter Maintenance option of the wizard allows the user to restore all
default filters and exceptions as well as delete all existing filters and
exceptions. The older way of filter management is also retained in the wizard as
the Legacy Filter Configuration task.
Lastly, the List All Firewall Policies task in the wizard displays all the
configured filters and exceptions so you can add or delete filters and
exceptions.
Advantages of the Firewall Wizard
Here are the main advantages of this tool, over using the existing filtcfg
and NBM Access Management:
Advantage 1: The logical grouping of services. BorderManager servers are
deployed in networks where there are different services and a number of servers
hosting them. The Firewall Wizard enables you to set up filter configurations
for these services in an organized way. Service exceptions can be set up based
on BorderManager services (such as proxy or VPN), on other Netware based
services (such as Groupwise, iFolder, iPrint, ZENWorks, etc.), or on services
running on servers other than the ones running BorderManager (proxy and VPN
services).
Earlier versions involved selecting exceptions from a large list. This
required you to know the specific exceptions required to access each service.
Now the wizard makes it easier because you only need to select the services
through the wizard, and the related exceptions and filters for the selected
service are added.
Advantage 2: Additional services. To access services such as Mail, Web, DNS
etc. running on a different server other than the BorderManager server, the
exceptions and filters can be easily configured. This is done through the
Off-Server Service exceptions option of the wizard.
Advantage 3: Consolidation of options. When you add exceptions and filters to
access the services, the wizard helps you navigate to these actions from a
single point. The options for Easy Filter Configuration, Filter Maintenance
(delete and restore defaults), Legacy Filter Configuration (for users familiar
with NBM Access Management) and List All Firewall Policies (for a list of what
exceptions have been configured) are all under a single heading. That makes it
easier to configure and control than the previous filter configuration
utilities.
Setting Up the Firewall Wizard
The new packet filtering configuration tasks are automatically plugged into
iManager when NBM 3.8 SP3 is installed. To bring up iManager for filter
configuration,
- Go to this URL: https://<IP Address or DNS of the
server>/nps/iManager.html
- Log in to iManager.
The Firewall Wizard options appear as an NBM Filter Management role on the
left pane of iManager.
Configuring Exceptions for Services using the Firewall Wizard
Easy Filter Configuration
Easy Filter Configuration has three main tabs (see the figure below): NBM
Service Exceptions, On-Server Service Exceptions, and Off-Server Service
Exceptions. Each of these tabs contain a list of services that have been grouped
based on their implementation and usage. These are explained in detail with some
typical scenarios below.
Figure 3 - Easy Filter configuration
NBM Service Exceptions Tab
This tab allows creation of service exceptions for Novell BorderManager Proxy
and VPN services. You select the proxy and VPN services for which filters and
exceptions need to be configured on the NBM server by the checking enable filter
button next to the required service. Then, the related service exceptions get
created on the server.
The Enable Log option enables logging for the selected services. However,
this logging option slows down server performance. Consider disabling logging
after you have tested your filters and exceptions.
The Stateful option is selected by default for all the service exceptions; it
can be unchecked if not required. Stateful filters can be enabled on less secure
applications that have no application gateways and therefore require security at
the packet filtering level. Secure apps like iFolder, iManager, iPrint etc.
would not require the stateful filtering to be enabled, which would reduce the
overhead at the IP stack level. For more details on this option, see the
Stateful IP Filters section of the following Tip:
http://www.novell.com/coolsolutions/Tip/7993.html
Below is a scenario where users in the internal LAN require access to the
public web and FTP server. Exceptions need to be created for HTTP, FTP and DNS
proxy services to allow the users in the protected network to access these
public resources located outside the firewall.
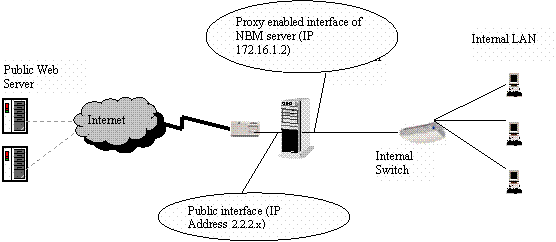
Figure 4 - Sample setup/scenario for NBM service exceptions
One interface of the BorderManager server is connected to the public internet
router and the other connects to the internal LAN for which forward proxy is
enabled on the NBM server.
To create the exceptions,
- Select HTTP, FTP and DNS services from the list of proxy services as shown
in Figure 4.
- Click Add to create exceptions for these services to be allowed through
the BorderManager server.
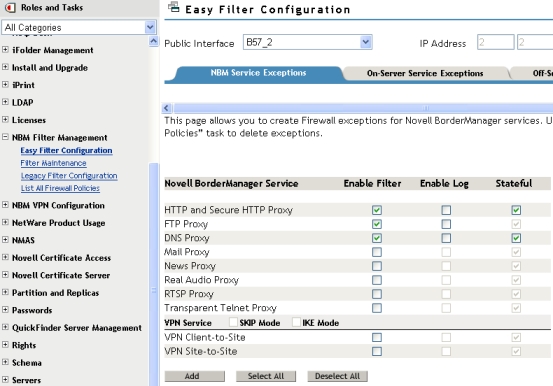
Figure 5 - Details of NBM service exceptions
Service exceptions are added for the outgoing requests as seen in Figure 6
below. Filters denying all other traffic to and from the public interface of the
NBM server are also added, along with the required service exceptions if not
already present. However, if these filters are already configured then they will
not be added again.
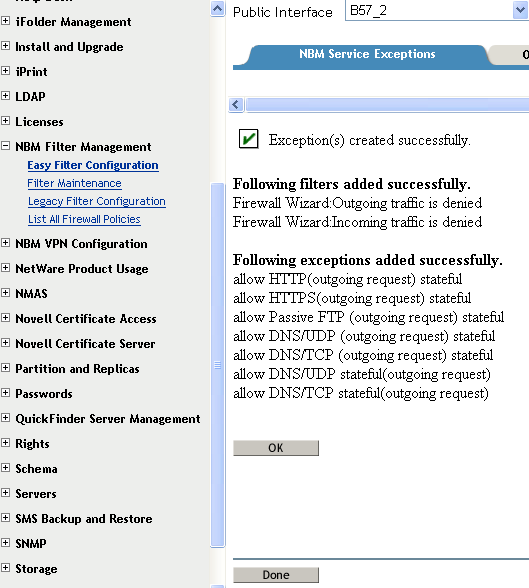
Figure 6 - List of exception created after selecting required services
from NBM service exceptions
Clicking OK directs you back to the main page (see Figure 5) instead of
displaying the list of policies configured above. To verify the list of policies
created, you only need to select the List All Firewall Policies option of the
wizard. This option displays the list of added filters and exceptions as shown
in Figure 7. 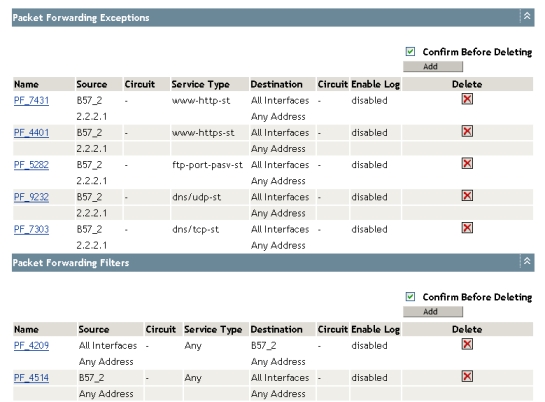
Figure 7 - List of the Firewall policies
On-Server Service Exceptions
On-Server Service Exceptions are a way to create exceptions for the selected
NetWare based services running on the BorderManager server.
These services include:
- File and print
- Mail and messaging
- Network management
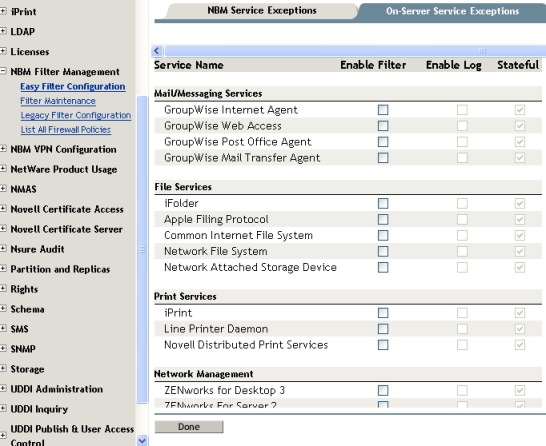
Figure 8 - Details of On-Server Service exceptions
Below is a sample setup that configures exceptions that allow iFolder access
on a BorderManager server, for clients located in the public network. 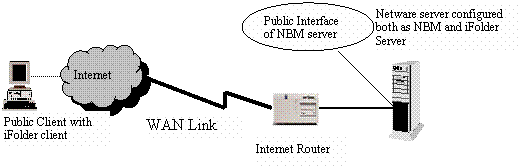
Figure 9 - Sample scenario for iFolder access on the NBM server
One interface of the NBM server is connected to the public Internet router.
This assumes, per the figure above, that users in the public network who have
iFolder client installed on their machine require access to the iFolder service.
That service is hosted on the NBM server.
To add service exceptions in this scenario,
- Select iFolder under File Services.
- Click Add to add the required exceptions for allowing the iFolder service
as shown in Figure 10.
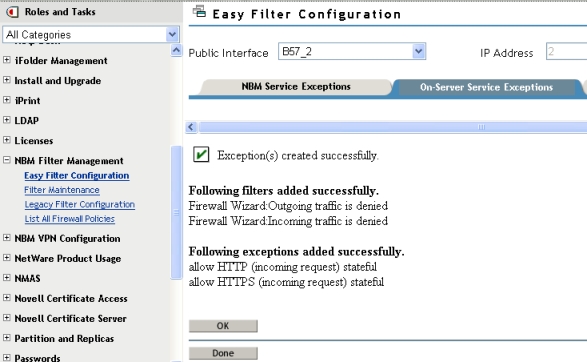
Figure 10 - Exceptions setup for iFolder access
Note: Selecting services such as iFolder, iPrint, Web Server and
iManager require only a single exception allowing port 443.
Off-Server Service Exceptions
This option adds service exceptions for services running on a
non-BorderManager server. This "other" server is identified by its IP address,
which needs to be provided under this option shown in the figure below.
This section lists all the Proxy and VPN services along with few other
services like Mail, Web, DNS etc. Here the proxy services can either be present
behind the firewall or outside the firewall. The related check boxes for both
the scenarios can be selected while configuring packet filters. This option is
not available for services such as Mail, Web, FTP, DNS and VPN. The figure below
shows all the available services with the options. 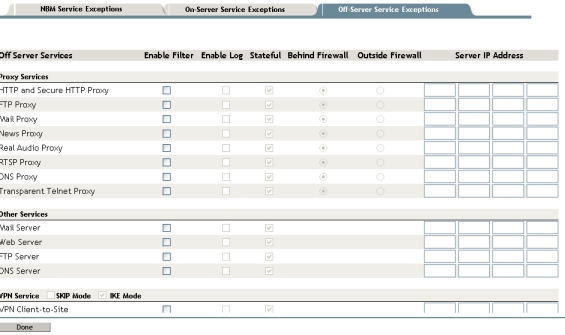
Figure 11 - Details of Off-Server Service exceptions
Below is a sample scenario to set up using Off-Server service
exceptions. 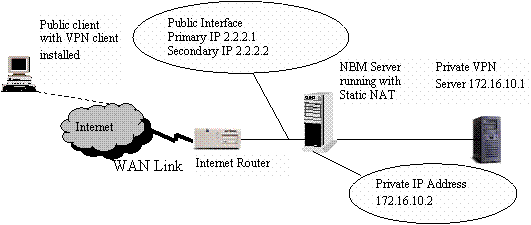
Figure 12 - Sample setup scenario for C2S VPN service running in the
private network
One interface of the NBM server is connected to public router, and the other
connects to the internal LAN that hosts the VPN server. Static NAT is enabled on
the NBM server to allow the clients in the public network to connect to the
private VPN server. The secondary IP address (2.2.2.2) of the NBM server is
statically mapped to the Private VPN server's IP address (172.16.10.1). This
allows the public client to connect to the private server using the statically
mapped public IP address (2.2.2.2).
To set up Off-Server exceptions in this scenario,
- Select VPN client-to-site from the VPN Services tab for IKE mode.
- Provide the IP address of the private VPN server.
Note: SKIP mode has also been provided for setting up exceptions for NBM
servers running versions below NBM 3.8. 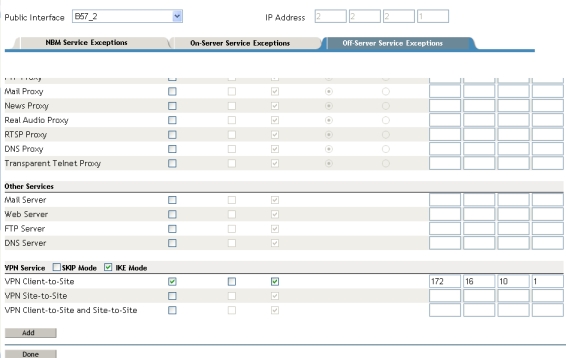
Figure 13 - VPN "Off-Server" services selected (running on a server
other than the NBM server which is configured for packet filtering)
The following service exceptions and filters will be added:  Figure 14 - List of exceptions created between the NBM server and any
other server
Figure 14 - List of exceptions created between the NBM server and any
other server
Filter Maintenance
This option restores any or all of the default filters. This works just like
the option of brdcfg that is available on NBM servers from NBM 3.7 SP3 onwards.
You can also clear all existing filters on the NBM server using this
option. 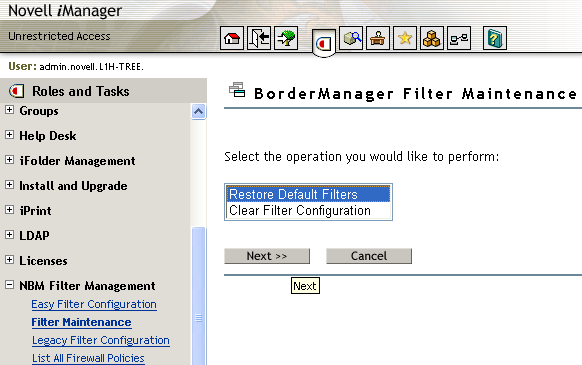
Figure 15 - Option for Filter maintenance
The Restore Default Filters sets up the list of filters shown below. This
list is similar to the list set up by running brdcfg on the public interface of
the NBM server. 
Figure 16 - List of default filters (same as running brdcfg)
- Select Clear All Filters to clear all existing filters as shown in the
figure below.
- Click OK if you want to clear all the filter configurations.

Figure 17 - Restoring or clearing filter configurations
Legacy Filter Configuration
This option has been present since NBM 3.7 as NBM Access Management. This
allows the user to create filters and exceptions by selecting the services from
the list of all available services.
List All Firewall Policies
This section lists all the configured service exceptions and filters as
selected under Easy Filter Configuration. You can add, delete or modify service
exceptions and filters here. Clicking Add here redirects you to the Legacy
filter configuration option to add service exceptions and filters. The checkbox
for Confirm before Deletion offers the option of prompting before deletion of
each filter or exception. If you want to delete an entire list of filters or
exceptions and don't want to be prompted several times, this option can be
unchecked. 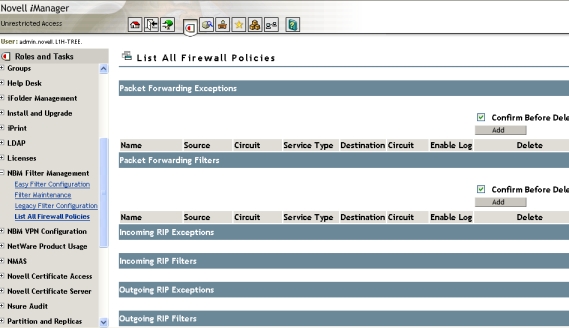
Figure 18 - List of all firewall policies
Troubleshooting
Problem: The Firewall wizard does not appear in iManager after
upgrading to NBM 3.8 SP3, or after an OS upgrade to a server that is already
running NBM 3.8 SP3.
Solution: Install bm.npm manually through iManager. This can be done
through the configure option of iManager as shown in the figure below: 
Figure 19 - Installing bm.npm manually through iManager
See the following link for a detailed understanding of installing, using, and
uninstalling Novell plug-in modules:
http://www.novell.com/documentation/imanager25/
Also make sure that the latest filtsrv.nlm is installed on the NBM
server.
Problem: The Public interface is not visible in iManager.
Solution: Mark the corresponding interface that connects to the public
Internet router as Public through filtcfg. That will cause these interfaces to
appear in the Firewall Wizard.
Problem: Cannot add service exceptions for multiple public
interfaces.
Solution: To add filters and exceptions through multiple public
interfaces on the NBM server mark them all as public through filtcfg. Then
select them from the public interfaces drop down list present on the top left
hand side of the wizard before selecting the relevant services that need to be
allowed through each of these interfaces.
Problem: Cannot access the Private VPN server behind the firewall from
outside after configuring the exceptions.
Solution: Check the server IP address you provided on the Off-Server
Service Exceptions option. Provide the Private VPN servers IP address here and
not the translated IP address. (Translated IP refers to the secondary IP address
on the public interface of the NBM server that has been statically mapped to the
Private VPN server's IP address.) Refer to the sample scenario described in the
Off-Server Service Exceptions section above to understand the setup for
this.
Known Limitations
- Naming and storing of filters: The names of the exceptions as displayed
under the List All Firewall Policies option is still in the "PF_xxxx" format
previously available with NBM Access Management.
- Interface assignment: The interfaces on the BorderManager need to be
explicitly assigned as Public and Private through the filtcfg utility.
- Only Public interfaces are displayed: The tool displays only the public
interfaces, which need to be previously marked as Public through filtcfg.
Hence, exceptions cannot be added for any other than the public interface.
- Backup option for filters: This needs to be done using the filtsrv_backup
utility from the command line on the NetWare (BorderManager) server.
Conclusion
This Tip describes implementation of packet filtering through iManager,
using the new Firewall Wizard provided with NBM 3.8 SP3 release. This wizard is
helpful to users who want to allow basic services through the firewall without
getting into the details of the protocols and ports that need to be selected for
allowing those services. This wizard makes filters/exceptions configuration much
easier.
The information in this Tip is derived strictly from test scenarios. In
real user scenarios, you may experience deviations from these results. Novell
does not recommend deploying directly in a production network. You should always
verify on a simulated test network before you deploy anything in a production
environment.
| 




